Archive - May 2021 Back
API Security
Posted on 19/5/2021 under tech api security

When I first learned how to develop APIs, my first question was how to secure them. I can't even deploy to production if I can't secure my APIs. Back then there wasn't alot of useful resources available to learn this. Recently there's been alot of question on how to secure apis floating around me.
Here are some of my layman thoughts on this.
Application level
1. Non public endpoints must be protected with Authorization and Authentication schemes, this is a must. An authorization service or app authenticates and issue access token / JWT.
2. Enforce HTTPS - this is a must
3. CORS settings - limit CORS to only allowed origins
4. Use JWT authenication parameters validation such as iss, aud, exp date
5. Validation of request headers parameters such as origin, referer, host or user agent if applicable
Network level
internet -> firewall -> load balancer -> apigateway -> firewall -> apis
1. If API is meant to be access not by public, implements firewall and whitelisting. Use WAF to control ip whitelisting, mitigate DDOS.
2. If api gateway is used, api apps server should only allow incoming traffic from api gateway.
3. Network traffic should be encrypted with TLS / using HTTPS
What do you think ?
More on Security - Man in Middle Attack (MIMA)
Posted on 20/5/2021 under tech api security
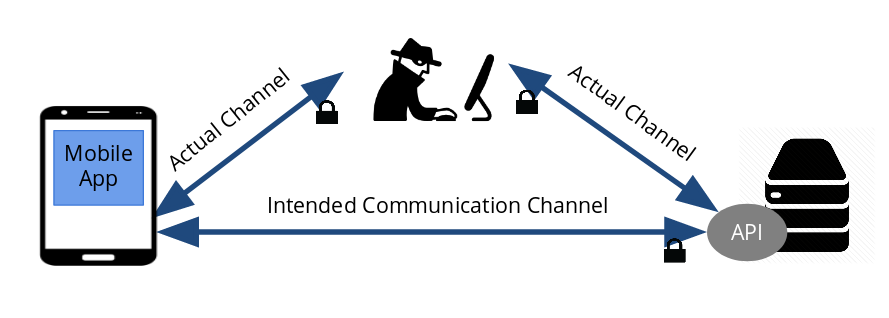
In my previous blog, I blogged on suggestions for securing APIs. However, I've been pondering on how to further secure against Man In Middle Attacks (MIMA). Even if API endpoints were protected via authorization/authentication scheme, the client access token can still be sniffed and intercept by man in the middle. Authentication process also requires credentials data to be posted in exchange for an access token, these credentials data can also be stolen by man in middle.
Design Considerations
In securing APIs, the must have basic security package would include
- Endpoints protected via Authorization/Authentication scheme
- Enforce use of HTTPS
On the client side such as mobile apps, we should consider
- SSL/TLS (Certificate) pinning - I will blog about this with pactical examples some time later
- Multi factor authenication functionality, if possible
Finally,
- safeguard against DDOS using WAF or some DDOS protection services
This would be at least, an overall good basic security package. What do you think ?
Time for supper. Peace and out.
Redis with ASP.NET Core for distributed sessions and horizontal scaling
Posted on 25/5/2021 under .net redis

Horizontal scaling is usually the preferred scaling solution to adopt, but they may not be feasible for web apps that relies on in-memory stores/caches for tracking session state or data. These apps needs to be re-architected to adopt the use of a distributed cache such as Redis to keep session data consistent across servers. Redis is usually use as a distributed cache or as a key-value in-memory database.
I'll provided the same source on how to set them up for the 2 difference use case. I will try to make some videos to explain step by step. Stay tune for updates.
Redis for distributed caching
For this case, Redis is configured as a cache and sessions is set up as well (refer to startup.cs). Any data set or read via HttpContext.Session (refer to the home controller) is set/read to/from the redis cache. Session data are typically used in web applications.
Redis as key-value database
In this case, Redis is set up and used like a database. The RedisContext class connects to Redis and provides all the get/set/delete functions to directly access the specificed keys in Redis. This implementation is more applicable to APIs, where session data are not likely to be used since APIs are stateless.
